Yesterday, I committed a new project to github. I wasn’t paying attention and made a (mental) typo in typing the jackson-databind version number. I typed 2.2.3 instead of 2.10.3. The former is an old version with security vulnerabilities.
This meant I got to try out a new feature I had only read about – github informing you about the security issue in a dependency. Looking at the repo, I saw a nice yellow box – “We found potential security vulnerabilities in your dependencies. Only the owner of this repository can see this message”
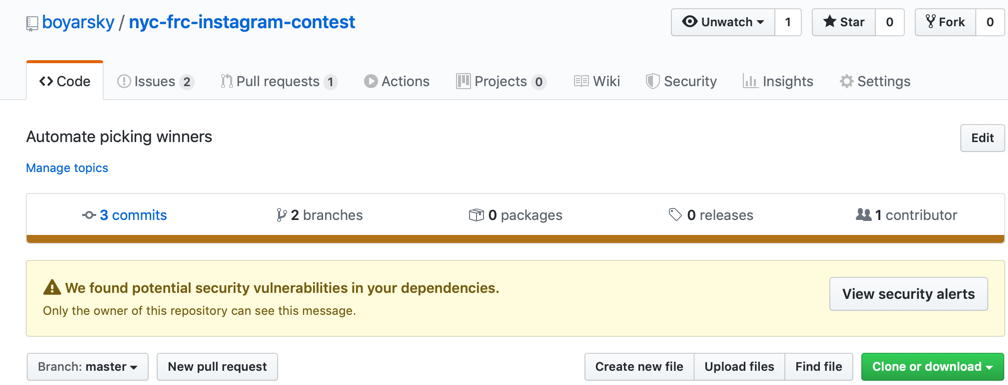
GitHub also created a pull request offering to “Bump jackson-databind from 2.2.3 to 2.9.10.3”. I chose not to accept the pull request and choose the later version I intended – 2.10.3.
After pushing that change, the yellow box went away. GitHub even noticed that I updated the pom.xml and closed the pull request with the message “Looks like com.fasterxml.jackson.core:jackson-databind is up-to-date now, so this is no longer needed.”.
I then went into my gmail and deleted the 18 emails with the subject “One of your dependencies has a security vulnerability.” All of these emails arrived within two hours after I committed. That’s way too many notifications!
